Modern Authentication is enabled by default for all new Microsoft 365/Azure tenants. This authentication protocol is more secure than the legacy Basic Authentication. Microsoft plans to completely block the use of Basic Authentication for all Microsoft 365 clients starting October 1, 2021. In this article, we’ll look at how to enable or disable Modern and Basic Authentication in Microsoft 365.
Modern Authentication vs. Basic Auth
Microsoft currently supports the following types of authentication for Office 365 (Microsoft 365):
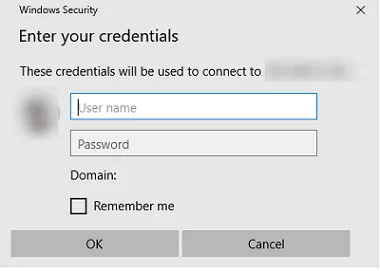
- Basic Authentication – this type of authentication is familiar to all Windows users. Basic auth is performed through a simple Windows Security window that prompts for a credential (username and password) and prompts you to save your password to the Windows Credential Manager. This authentication type doesn’t support MFA (Multifactor Authentication) and is not robust against brute-force attacks. Applications store and explicitly use the username and password for authentication.
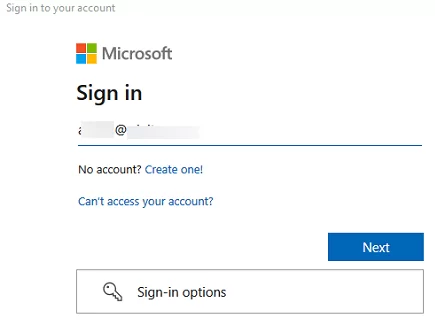
- Modern Authentication is based on ADAL (Active Directory Authentication Library) and OAuth 2.0 protocols. Apps don’t store or use user credentials, and authentication is based on time-limited tokens. Modern Auth supports additional authentication factors including MFA. The window for entering a username and password when performing modern authentication looks like this. It will appear when connecting to Microsoft 365 services or connecting to Azure (including PowerShell connections).
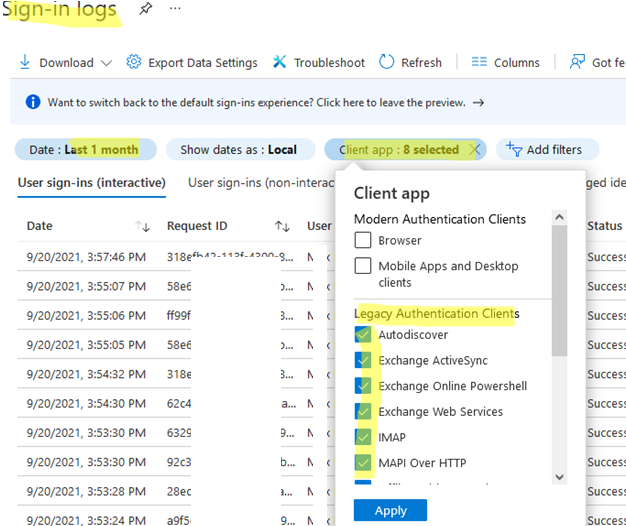
Basic Authentication Sign-in Log in Azure AD
Before enabling modern authentication and disabling basic authentication, check which authentication protocols your Microsoft 365 users and apps use.
- Open the Azure Portal;
- Go to the Azure Active Directory -> Sign-in logs;
- Select the date range Last 1 month;
- Add filter by field Client App;
- Select all Legacy Authentication Clients for this filter.
This will allow you to find users and applications that are still using Basic Authentication. You need to migrate the found applications to the Modern Auth protocol. In my case, most of the events were associated with native email clients on smartphones, they need to be migrated to the MS Outlook app.
Microsoft automatically disables Basic Authentication for tenants where it is not used.
How to Enable Modern Authentication for Microsoft 365 Tenant?
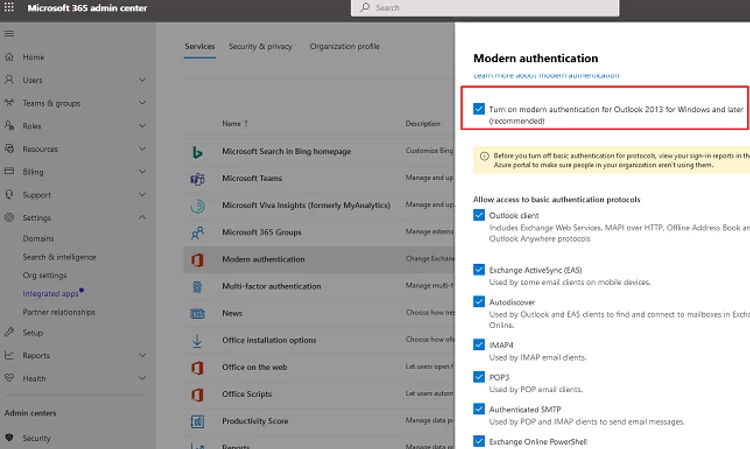
You can enable Modern Authentication through the Microsoft 365 Admin Center.
- Open the M365 Admin portal https://admin.microsoft.com;
- Go to Settings -> Org Settings -> Modern authentication
- Enable the option Turn on modern authentication for Outlook 2013 for Windows and later;
- Save the changes.
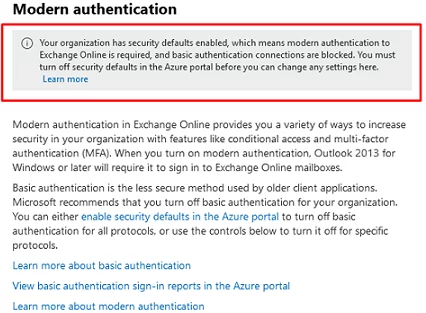
As we mentioned, for new Office 365/Azure tenants, Basic Authentication is disabled by default for all apps. In this case, a warning will be displayed in this section:
Your organization has security defaults enabled, which means modern authentication to Exchange Online is required, and basic authentication connections are blocked. You must turn off security defaults in the Azure portal before you can change any settings here.
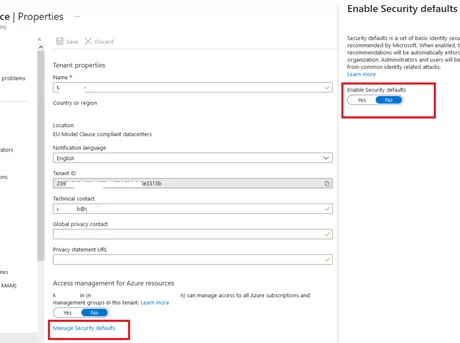
You can enable Basic Auth support for a tenant from the Azure portal (Azure Active Directory -> Properties -> Manage Security defaults -> Enable Security defaults = No).
Note a number of options under Allow access to basic authentication protocols. Here are the various applications where you can enable Basic Authentication.
- Outlook client
- Exchange ActiveSync (EAS)
- Autodiscover
- IMAP4
- POP3
- Authenticated SMTP (example of SMTP authentication from telnet)
- Exchange Online PowerShell — (Basic Authentication is not supported for modern EXOv2 PowerShell Module)
Disable Basic Authentication for all apps and protocols that definitely don’t need it.
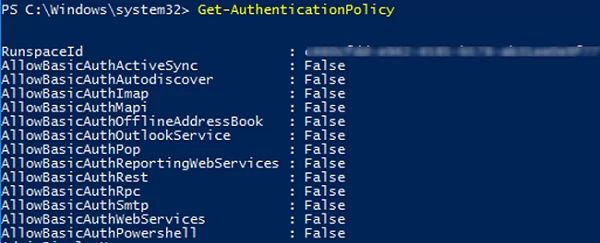
If you have authentication policies configured in your Office 365 tenant, you can display the current settings and protocols that are allowed to use Basic Authentication. Use the following PowerShell command:
Get-AuthenticationPolicy
In our case, we have only one policy and BasicAuth is disabled for all apps.
AllowBasicAuthActiveSync : False AllowBasicAuthAutodiscover : False AllowBasicAuthImap : False AllowBasicAuthMapi : False AllowBasicAuthOfflineAddressBook : False AllowBasicAuthOutlookService : False AllowBasicAuthPop : False AllowBasicAuthReportingWebServices : False AllowBasicAuthRest : False AllowBasicAuthRpc : False AllowBasicAuthSmtp : False AllowBasicAuthWebServices : False AllowBasicAuthPowershell : False
For security purposes, you can create a separate policy with different Basic Auth permissions for specific protocols and assign it to users using the legacy application. In this example, we’ll allow a user to connect to Exchange Online through a remote PowerShell session with basic authentication:
Set-AuthenticationPolicy -Identity "BasicAuth_Allow_PoSh" -AllowBasicAuthPowershell:$true
Set-User -Identity k.muller -AuthenticationPolicy "BasicAuth_Allow_PoSh"
And the default policy will block legacy auth protocol:
New-AuthenticationPolicy -Name "BasicAuth_Block"
Set-OrganizationConfig -DefaultAuthenticationPolicy BasicAuth_Block
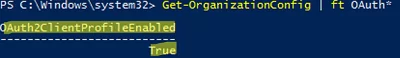
Also, note that there is another OAuth2ClientProfileEnabled option in the organization settings, which determines whether Modern Auth is enabled for the tenant:
Get-OrganizationConfig | ft OAuth*
If OAuth2ClientProfileEnabled = False, it means that modern authentication is disabled.
Modern Authentication in Outlook 365/2019/2016/2013/2010
Please note the specifics of support for modern authentication in different Outlook versions:
- Outlook 2010 and earlier – don’t support Modern Auth. If Basic Auth is disabled in the tenant settings, these versions of Outlook won’t be able to connect to Exchange Online mailboxes on Microsoft 365;
- Outlook 2013 – to support OAuth, you need to set two registry parameters under the key HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\15.0\Common\Identity (
EnableADAL = 1andVersion = 1; - Outlook 365, 2019, 2016 – modern authentication is supported by default. In order to always use Modern Auth first, set the
AlwaysUseMSOAuthForAutoDiscover = 1under the reg key HKEY_CURRENT_USER\Software\Microsoft\Exchange (if this option is not enabled, Outlook may continually prompt for the password to connect);
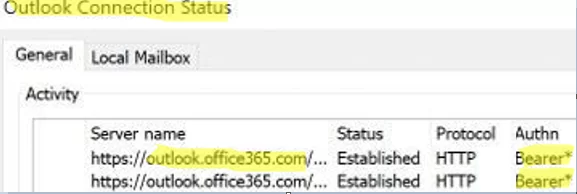
You can verify that the Outlook client is using Modern Authentication to connect to Office 365 mailbox. Hold Ctrl and click on the Outlook icon in the tray. Make sure Bearer* is specified in the Authn field in the Outlook Connection Status. This means Outlook is using modern authentication.
1 comment
The Exchange Team:
Today, we are announcing that, effective October 1, 2022, we will begin to permanently disable Basic Auth in all tenants, regardless of usage, with the exception of SMTP Auth.
IMPORTANT: Beginning early 2022, we will selectively pick tenants and disable Basic Auth for all affected protocols except SMTP AUTH for a period of 12-48 hours. After this time, Basic Auth for these protocols will be re-enabled, if the tenant admin has not already re-enabled them using our self-service tools.