You can enable, disable, or get the Multi-Factor Authentication (MFA) status for users in your Azure/Microsoft 365 tenant using Azure Portal, Microsoft 365 Admin Center, or PowerShell. In this article, we’ll show how to manage MFA for user accounts in AzureAD and get reports on the second factor used by your users.
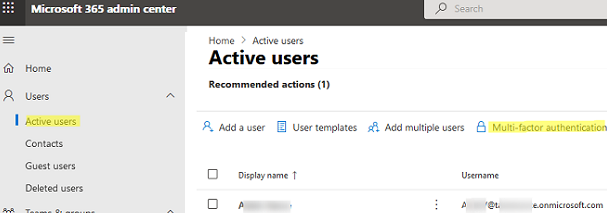
You can access a web page with the MFA status for all users in two ways:
- Microsoft 365 Admin Center -> Active Users -> Multi-factor authentication.
- Portal Azure -> Azure AD-> Users -> Per-user MFA
You will see a list of all users in your tenant and the MFA status for each of them. Available MFA statuses are:
- Disabled – multi-factor authentication is disabled (by default, for all new users);
- Enabled – MFA is enabled, but a user is still using standard authentication until they select the MFA method themselves;
- Enforced – a user will be forced to register a second MFA factor at the next logon.
You can enable, disable, reset, or configure MFA for each user using buttons in the Quick Steps panel on the right.
The report doesn’t show if a user completed the MFA setup and which second factor he has selected. Also, you cannot export the contents of the page to a TXT/CSV file. It is easier to use PowerShell to manage users’ MFA in Microsoft 365 and build reports.
Now you can enable/disable MFA for Azure (Microsoft 365) users in PowerShell using the MSOnline module or Microsoft Graph API.
Install the MSOnline module (if needed) and connect to your tenant:
Install-Module MSOnline
Connect-MsolService
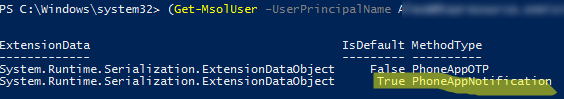
You can get the information about user MFA status from the StrongAuthenticationMethods attribute:
Get-MsolUser –UserPrincipalName [email protected] | Select-Object UserPrincipalName,StrongAuthenticationMethods
If the StrongAuthenticationMethods attribute is not empty, then MFA is enabled for the user. You can find out what type of MFA is configured for the user:
(Get-MsolUser –UserPrincipalName [email protected]). StrongAuthenticationMethods
The screenshot below shows that the user has Microsoft Authenticator App enabled as a second MFA factor (PhoneAppNotification — IsDefault=True ).
Microsoft Modern authentication allows four types of authentication as a second factor for users:
- OneWaySMS – standard SMS message;
- TwoWayVoiceMobile – a user gets a one-time password in a phone call;
- PhoneAppOTP – a user gets a one-time password (6 digital characters) using a hardware token or Microsoft Authenticator app;
- PhoneAppNotification – authentication using the Microsoft Authenticator app.
To enable MFA for an Azure user:
$st = New-Object -TypeName Microsoft.Online.Administration.StrongAuthenticationRequirement
$st.RelyingParty = "*"
$st.State = "Enabled"
$sta = @($st)
Set-MsolUser -UserPrincipalName t.mull[email protected] -StrongAuthenticationRequirements $sta
To force a user to change their current MFA method:
Set-MsolUser -UserPrincipalName [email protected] -StrongAuthenticationMethods @()
To disable MFA for a user:
Get-MsolUser -UserPrincipalName [email protected] | Set-MsolUser -StrongAuthenticationRequirements @()
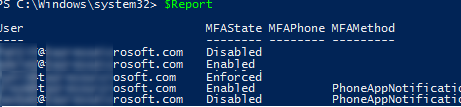
You can use the following PowerShell script to get the MFA status for all users in an Azure tenant:
$Report = @()
$AzUsers = Get-MsolUser -All
ForEach ($AzUser in $AzUsers) {
$DefaultMFAMethod = ($AzUser.StrongAuthenticationMethods | ? { $_.IsDefault -eq "True" }).MethodType
$MFAState = $AzUser.StrongAuthenticationRequirements.State
if ($MFAState -eq $null) {$MFAState = "Disabled"}
$objReport = [PSCustomObject]@{
User = $AzUser.UserPrincipalName
MFAState = $MFAState
MFAPhone = $AzUser.StrongAuthenticationUserDetails.PhoneNumber
MFAMethod = $DefaultMFAMethod
}
$Report += $objReport
}
$Report
You can export the MFA report to a CSV file:
$Report| Export-CSV -NoTypeInformation -Encoding UTF8 c:\Reports\AzureUsersMFAstatus.csv
Or into an Out-GridView table:
$Report | Out-GridView
The script is available in my GitHub repository: https://github.com/maxbakhub/winposh/blob/main/Azure/GetAzureMFAUsersReport.ps1

1 comment
Hello
Is there a script to enforce MFA in bulk (change from Enabled to Enforced or even from Disabled to Enforced)?