In order to grant local administrator permissions on domain computers to technical support personnel, the HelpDesk team, certain users, and other privileged accounts, you must add the necessary Active Directory users or groups to the local Administrators group on servers or workstations. In this article, we’ll show you how to manage members of the local Administrators group on domain computers manually and through GPO.
Add a User to the Local Admins Group Manually
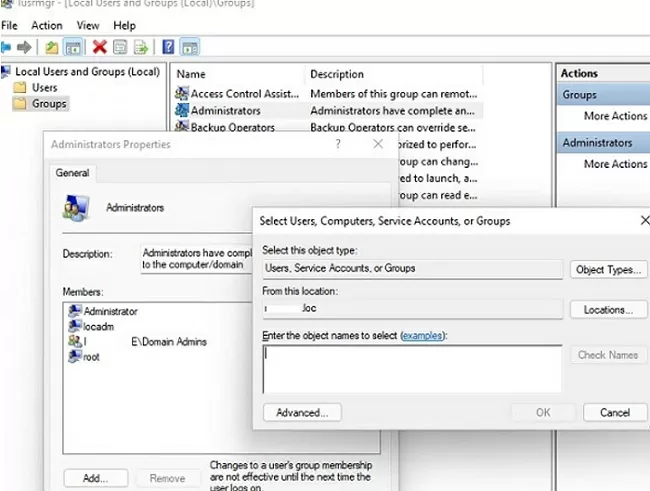
The easiest way to grant local administrator rights on a specific computer for a user or group is to add it to the local Administrators group using the graphical Local Users and Groups snap-in (lusrmgr.msc).
When you join a computer to an AD domain, the Domain Admins group is automatically added to the computer’s local Administrators group, and the Domain User group is added to the local Users group.
Click the Add button and specify the name of the user, group, computer, or service account (gMSA) that you want to grant local administrator rights. With the Location button, you can switch between searching for principals in the domain or on the local computer.
You can also display a list of users with local computer administrator permissions with the command prompt:
net localgroup administrators
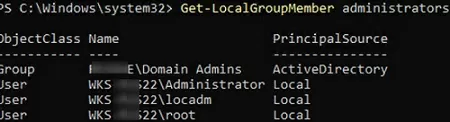
You can use the following PowerShell command to get a list of users in a local group (using the built-in LocalAccounts module to manage local users and groups):
Get-LocalGroupMember administrators
This command shows the object class that has been granted administrator permissions (ObjectClass = User, Group, or Computer) and the source of the account or group (ActiveDirectory, Azure AD, Microsoft, or Local).
To add a domain group munWksAdmins (or user) to the local administrators, run the command:
net localgroup administrators /add munWksAdmins /domain
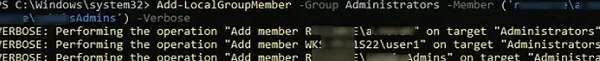
Using PowerShell, you can add a user to administrators as follows:
Add-LocalGroupMember -Group Administrators -Member ('woshub\j.smith', 'woshub\munWksAdmins','wks1122\user1') –Verbose
In this example, we added a user and groups from the woshub domain and a local user wks1122\user1 to the computer administrators.
You can add users to the Administrators group on multiple computers at once. In this case, you can use the Invoke-Command cmdlet from PowerShell Remoting to access the remote computers over a network:
$WKSs = @("PC001","PC002","PC003")
Invoke-Command -ComputerName $WKSs –ScriptBlock {Add-LocalGroupMember -Group Administrators -Member woshub\munWksAdmins'}
In an Active Directory domain environment, it is better to use Group Policy to grant local administrator rights on domain computers. This is much easier, more convenient, and safer than manually adding users to the local Administrators group on each computer. You can use two Group Policy options to manage the Administrators group on domain computers:
- Manage local group membership with Group Policy Preferences;
- Adding users to local groups using the Restricted Groups GPO feature.
How to Add Domain Users to Local Administrators via Group Policy Preferences?
Group Policy Preferences (GPP) provide the most flexible and convenient way to grant local administrator privileges on domain computers through a GPO.
Let’s say your task is to grant local administrator privileges on computers in a specific Active Directory OU (Organizational Unit) to a HelpDesk team group. Create a new security group in your domain using PowerShell and add the Helpdesk team accounts to it:
New-ADGroup munWKSAdmins -path 'OU=Groups,OU=Munich,OU=DE,DC=woshub,DC=com' -GroupScope Global –PassThru
Add-AdGroupMember -Identity munWKSAdmins -Members amuller, dbecker, kfisher
Open the domain Group Policy Management console (GPMC.msc), create a new policy (GPO) AddLocaAdmins and link it to the OU containing computers (in my example, it is ‘OU=Computers,OU=Munich,OU=DE,DC=woshub,DC=com’).
- Edit the AddLocaAdmins GPO you created earlier;
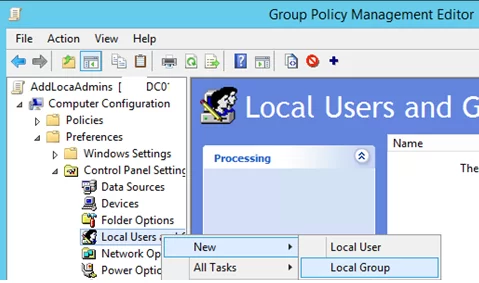
- Go to the following GPO section: Computer Configuration –> Preferences –> Control Panel Settings –> Local Users and Groups;
- Add a new rule (New -> Local Group);
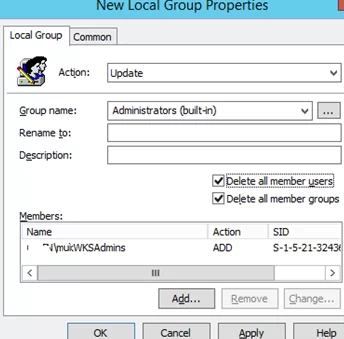
- Select Update in the Action field (it is an important option!);
- Select Administrators (Built-in) in the Group Name dropdown list. Even if this group has been renamed on the computer, the settings will be applied to the local Administrators group by its SID (
S-1-5-32-544); - Click the Add button and select the groups you want to add to the local Administrators group (in our case, this is munWKSAdmins);You can remove all manually added users and groups from the local Administrators on all computers. Check the “Delete all member users” and “Delete all member groups” options. In most cases, it is reasonable because you guarantee that only the approved domain groups will have administrator permissions on your domain computers. If you add a user to the Administrators group manually using the “Local users and groups” snap-in, it will be automatically removed next time when the policy is applied.
- Save the policy and wait for it to be applied to the client workstations. To apply the Group Policy settings immediately, run this command
gpupdate /forceon a user’s computer; - Open the
lusrmgr.mscsnap-in on any domain computer and check the local Administrators group members. Only the munWKSAdmins group should be added to this group, while other users and groups will be removed (except for the built-in Windows Administrator account).
Adding a Single User to the Local Admins Group on a Specific Computer with GPO
Sometimes you may need to grant a single user the administrator privileges on a specific computer. For example, you have several developers who need elevated privileges from time to time to test drivers, debug or install them on their computers. It is not reasonable to add them to the group of workstation adminis with privileges on all domain computers.
You can use GPO WMI filters or Item-level Targeting to grant local admin permission on a specific computer.
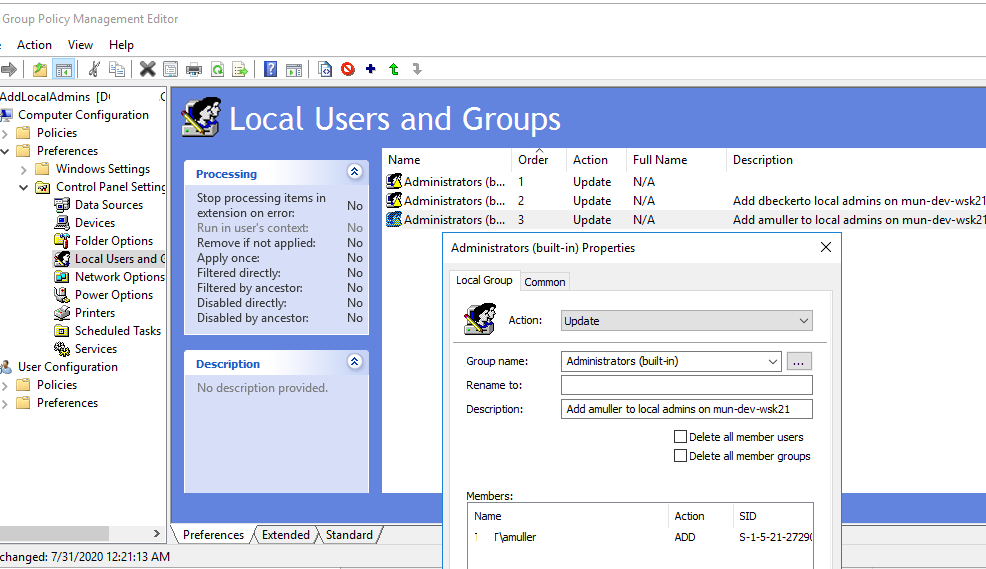
Create a new entry in the GPO preference section (Computer Configuration –> Preferences –> Control Panel Settings –> Local Users and Groups) of AddLocalAdmins policy created earlier:
- Action:
Update - Group Name:
Administrators (Built-in) - Description: “
Add amuller to the local administrators on the mun-dev-wsk21 computer” - Members: Add ->
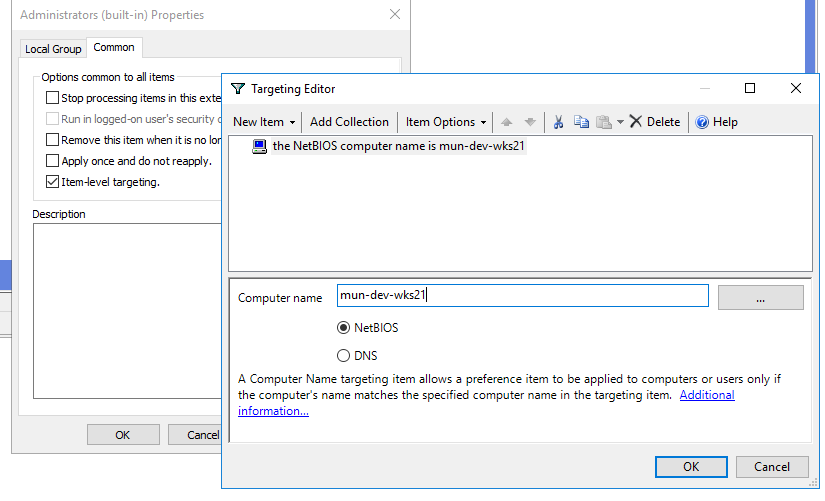
amuller - In the Common -> Targeting tab, specify this rule: “
the NETBIOS computer name is mun—dev-wks24.” It means that this Group Policy item will be applied only to the computer specified here.
Also, note the order in which group membership is applied on the computer (the Order GPP column). Local group membership is applied from top to bottom (starting from the Order 1 policy).
The first GPP policy option (with the “Delete all member users” and “Delete all member groups” settings as described above) removes all users/groups from the local Administrators group and adds the specified domain group. Then the additional computer-specific policies are applied that add the specified user to the local admins. If you want to change the membership order in your Administrators group, use the buttons on top of your GPO Editor console.
Managing Local Admins with Restricted Groups GPO
The Restricted Groups policy also allows adding domain groups/users to the local security group on computers. This is an older method of granting local administrator privileges and is used less often now (it is less flexible than the Group Policy Preferences method described above).
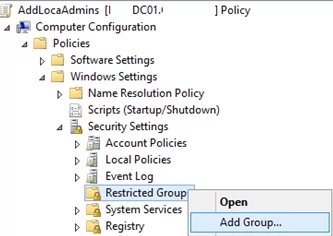
- Open your GPO;
- Expand the section Computer Configuration -> Policies -> Security Settings -> Restricted Groups;
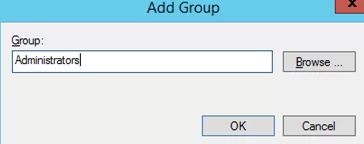
- Select Add Group in the context menu;
- In the next window, type Administrators and then click OK;
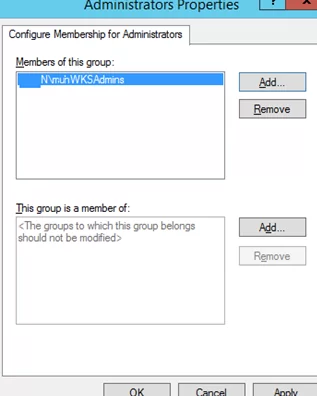
- Click Add in the Members of this group section and specify the group you want to add to the local admins;
- Save the changes, apply the policy to users’ computers, and check the local Administrators group. It must contain only the group you have specified in the policy.These Group Policy settings always (!) remove all existing members of the local Administrators group (which are added manually, by other policies or scripts).
If you need to keep the current membership of the Administrators group and add an additional group (user) to it using Restricted Groups GPO, you need to:
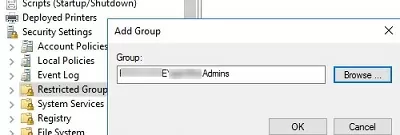
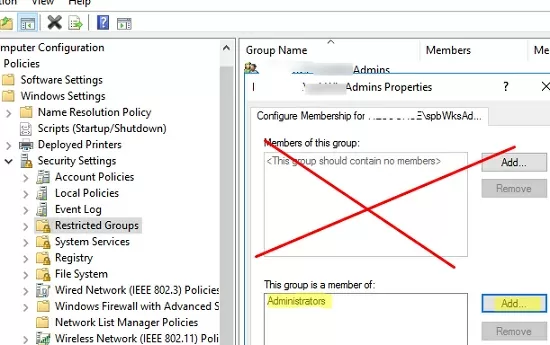
- Create a new entry in Restricted Groups and select the AD security group (!!!) that you want to add to the local admins;
- Then add the Administrators in the This group is a member of section;
- Update the GPO settings on the client and make sure your domain group has been added to the local Administrators group. In this case, the current principals in the local group stay untouched (not removed from the group).
At the end of the article, I will leave some recommendations for managing administrator permission on Active Directory computers and servers.
Microsoft’s classic security best practices recommend using the following groups to separate administrator permissions in an AD domain:
- Domain Admins are used only on domain controllers;From the security point of view for privileged administrator accounts, it is not recommended to perform daily administration tasks on workstations and servers under an account with the Domain Admin privileges. These accounts must be used only for AD management tasks (adding new domain controllers, replication management, Active Directory schema modification, etc.). Most user, computer, or GPO management tasks must be delegated to regular administrator accounts (without Domain Admin permissions). Do not use Domain Admin accounts to log on to any workstations or servers other than domain controllers.
- Server Admins is a group that allows managing the Windows Server hosts in an AD domain. Must not be a member of the Domain Admins group or local Administrators group on workstations;
- Workstation Admins is a group for performing administrative tasks on workstations only. Must not be a member of the Domain Admins and Server Admins groups;
- Domain Users are common user accounts to perform typical office operations. They must not have administrator privileges on servers or workstations;
- It is not recommended to add individual user accounts to the local Administrators group. It is better to use the domain security groups. In this case, in order to grant administrator privileges to the next tech support employee, it is enough to add him to the domain group (without the need to edit the GPO).
11 comments
Thank you. This site is a gem.
Nice clear article.
but I have found a interesting behavior where adding user(s) or group(s) using the GPO Preference control panel works perfectly on Domain Members, but does not work at all on Domain Controllers.
I’m also not very clear if we can use a wildcard with the Netbios computer name is *TEST*
In the sense that I want only to target the server with the word TEST in their name
Domain Controllers dont have local groups. In the computer management snapin you dont even see it anymore on a domain controller. Also in my experience the NETBIOS item level targeting does not work at all, if it is a single client that needs a special admin, just do it manually.
Amzing. Helped me for exact GPO
Great write up man! Exactly what I needed with clear instructions.
Very much appreciated.
The description mentioned in “Adding a Single User to the Local Admins Group on a Specific Computer with GPO” in step 3 is the description of the group which you see in the local mmc under “Local Users and Groups”. So you maybe don’t want “Add amuller to the local administrators on the mun-dev-wsk21 computer” as description for the local administrator group :).
Great explantation thanks a lot, I have one tricky question. How can I know which admin account have added a member into this administrator group ? I tried on the event log (ID 4728, 4732, 4746, 4751, 4756, 4761) but I don’t find the responsible of theses actions.
Could I use something like this to add domain users to a specific AD security group?
Use PowerShell to add users to AD groups. Why would you want to use a GPO to do this?
Add-AdGroupMember -Identity TestADGroup -Members user1, user2https://woshub.com/active-directory-group-management-using-powershell/
Hi Guys,
As always, thank you very much for your help and guidance.
I have applied this in my testing environment but i am not able to see the GPO when i do a gpresult /r.
The gpo is deployed to authenticated users.
I have added domain computers and authenticated users as read.
The scenario that i am testing is adding a user to the local admin group.
COuld you please help me understand what am i missing?
Thank you and best.
Peace.
One more thing, I can confirm that it is working, however, the rights are removed after a gpupdate /force, is this normal?