In this article, we’ll look at how to delegate administrative permissions in the Active Directory domain. Delegation allows you to grant the permissions to perform some AD management tasks to common domain (non-admin) users without making them the members of the privileged domain groups, like Domain Admins, Account Operators, etc. For example, you can use delegation to grant a certain AD security group (say, Helpdesk) the permissions to add users to groups, create new users in AD, and reset the account passwords.
Understanding Active Directory Delegated Permissions
To delegate permissions in AD, the Delegation of Control Wizard in the Active Directory Users and Computers console (DSA.msc) is used.
You can delegate administrative privileges in AD on a fairly granular level. You can grant one group the permission to reset passwords in the OU, another one – to create and delete user accounts, and the third one – to create and change group membership. You can configure permission inheritance on the nested OUs. Permissions can be delegated in Active Directory on the following levels:
- AD site;
- The whole domain;
- A specific Organizational Unit (OU) in Active Directory;
- A specific AD object.
Best practices for delegation control in Active Directory:
- It is not recommended to delegate (assign) permissions directly to specific user accounts. Create a new security group in AD instead, add a user to it, and delegate permissions on an OU for that group. If you want to grant the same permissions to another user, you can simply add him to this security group;
- Avoid using Deny permissions, as they take precedence over allowed ones;
- Periodically audit the delegated permissions in the domain (a report with the current lists of permissions per OU can be created using PowerShell);
- Do not grant anyone permissions to manage the OU with the administrator accounts. Otherwise, any support staff member can reset the domain administrator password. All privileged users and groups should be placed to a separate OU that is not subject to delegation rules.
Delegate Password Reset and Unlock Account Permissions in AD
Let’s imagine that your task is to grant the HelpDesk group the permissions to reset passwords and unlock user accounts in the domain. Let’s create a new security group in AD using PowerShell:
New-ADGroup "HelpDesk" -path 'OU=Groups,OU=Paris,OU=Fr,dc=woshub,DC=com' -GroupScope Global
Add users you want to this group:
Add-AdGroupMember -Identity HelpDesk -Members rdroz, jdupont
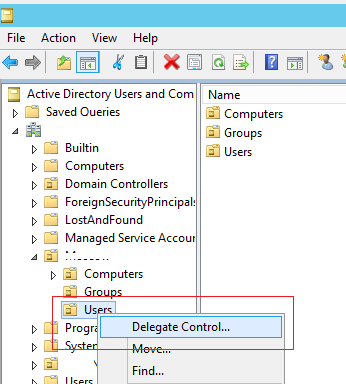
Run the Active Directory Users and Computers mmc snap-in (dsa.msc), right-click the OU with the users (in our example it is ‘OU=Users,OU=Paris,OU=Fr,dc=woshub,DC=com’), and select the Delegate Control menu item.
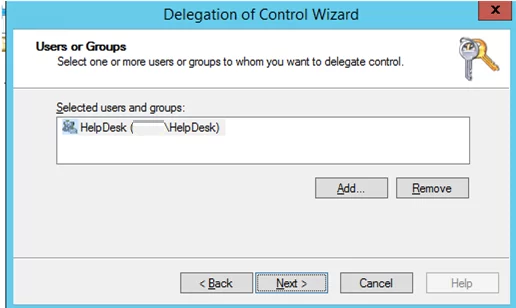
Select the group you want to grant administrative privileges to.
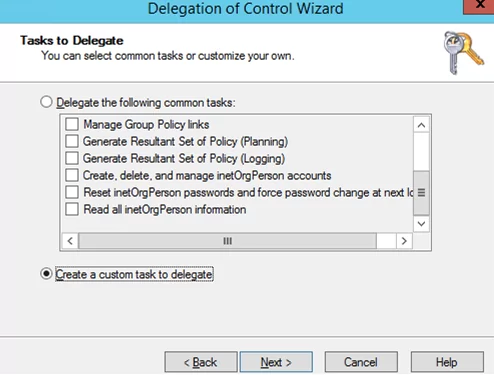
Select one of the preconfigured set of privileges (Delegate the following common tasks):
- Create, delete, and manage user accounts;
- Reset user passwords and force password change at next logon;
- Read all user information;
- Create, delete and manage groups;
- Modify the membership of a group;
- Manage Group Policy links;
- Generate Resultant Set of Policy (Planning);
- Generate Resultant Set of Policy (Logging);
- Create, delete, and manage inetOrgPerson accounts;
- Reset inetOrgPerson passwords and force password change at next logon;
- Read all inetOrgPerson information.
Or create a custom task to delegate. I choose the second option.
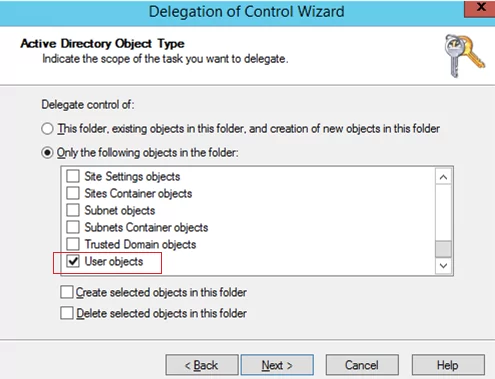
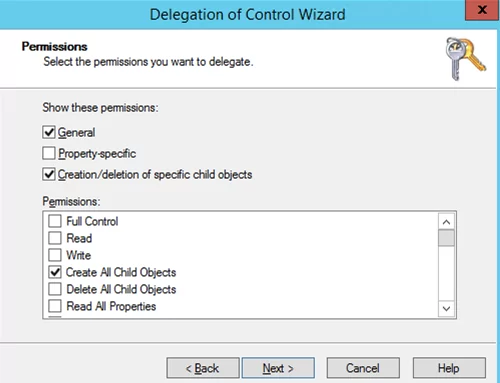
Select the type of AD objects you want to grant administrative permissions to. Since we want to grant control over user accounts, select the User Object item. If you want to grant the permissions to create or delete users in the OU, select the options Create/Delete selected objects in this folder. In our example, we don’t grant such privileges.
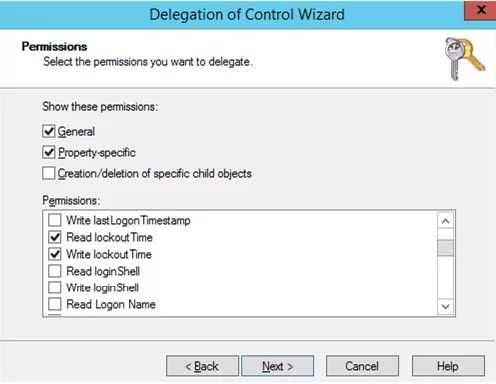
In the list of permissions, select the ones you want to delegate. In our example, we’ll select the privileges to unlock user accounts (Read lockoutTime and Write lockoutTime) and to reset a password (Reset password).
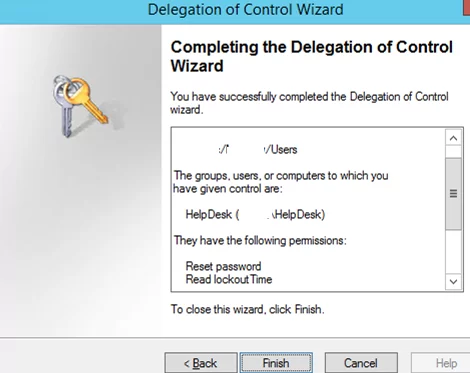
Click Next, and confirm the delegation of the selected permissions on the last screen.
Now, under a user account from the HelpDesk group try to reset a password of the user from the target OU using PowerShell:
Set-ADAccountPassword gchaufourier -Reset -NewPassword (ConvertTo-SecureString -AsPlainText “P@ssdr0w1” -Force -Verbose) –PassThru
The password should reset successfully (if it matches the domain password policy).
Now try to create a user in this OU using the New-ADUser cmdlet:
New-ADUser -Name gmicheaux -Path 'OU=Users,OU=Paris,OU=FR,DC=woshub,DC=com' -Enabled $true
An access denied error should appear since you haven’t delegated the rights to create new AD accounts.
You can use domain controller security logs to audit the actions of users to whom you have delegated administrative permissions. For example, you can track who reset a user password in the domain, who created a user account in AD, or track changes in sensitive AD groups.
Delegate Permissions to Join Computers to AD Domain
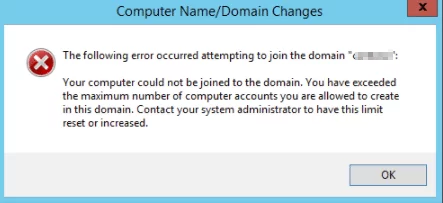
By default, any domain user can join up to 10 computers to the domain. When adding the 11th computer, an error will appear:
Your computer could not be joined to the domain. You have exceeded the maximum number of computer accounts you are allowed to create in this domain. Contact your system administrator to have this limit reset or increased.
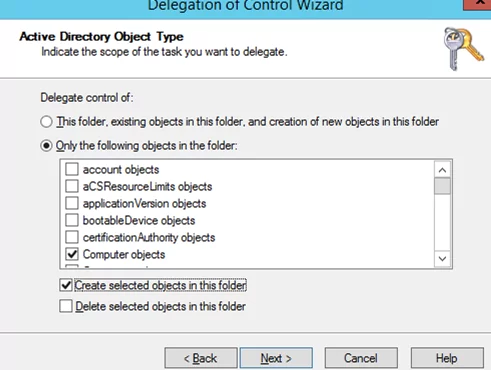
You can change this restriction on the domain-wide level by increasing the value of the ms-DS-MachineAccountQuota attribute. Or (which is more correct and secure) by delegating the permissions to join computers to a certain OU to a specific user group (helpdesk). To do this, delegate the permissions to create objects of Computer objects type. In the Delegation of Control Wizard, select Create selected objects in this folder.
Select Create All Child Objects in the Permissions section.
If you want to delegate the right to move objects between Organizational Units in AD, you must grant the following permissions: Delete User objects, Write Distinguished Name, Write name (**), Create User (or Computer) objects.
How to View and Remove Delegated Permissions in Active Directory?
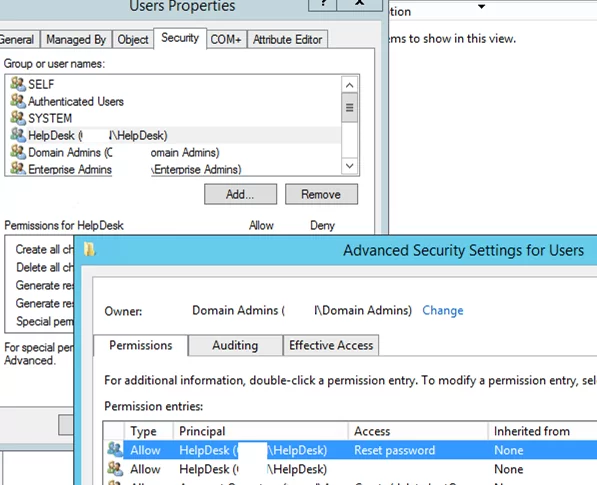
Any number of delegation rules can be assigned to an OU in AD. You can get a list of groups and the permissions delegated to them in the properties of the OU in the ADUC console. Go to the Security tab.
This contains a list of AD subjects that have been granted permissions for this container. You can see the list of granted permissions on the Advanced tab. As you can see, the HelpDesk group is allowed to reset passwords.
You can revoke a specific group of administrative permissions previously assigned through delegation. Find the name of the group you delegated permissions to and click Remove.
In addition, on the Security -> Advanced tab you can manually assign delegated permissions to different security groups.
How to Delegate Permissions in Active Directory with PowerShell?
You can get a list of permissions that are delegated to the OU or change the current permissions using PowerShell. The Get-ACL and Set-ACL cmdlets are used to view and change permissions in Active Directory (the same PowerShell cmdlets are used to manage NTFS permissions on files and folders).
The following simple script will list all non-standard permissions that are delegated to a specific organizational unit in AD:
# get the OU
$OUs = Get-ADOrganizationalUnit -Filter 'DistinguishedName -eq "OU=Users,OU=Paris,DC=woshub,DC=com"'| Select-Object -ExpandProperty DistinguishedName
$schemaIDGUID = @{}
$ErrorActionPreference = 'SilentlyContinue'
Get-ADObject -SearchBase (Get-ADRootDSE).schemaNamingContext -LDAPFilter '(schemaIDGUID=*)' -Properties name, schemaIDGUID |
ForEach-Object {$schemaIDGUID.add([System.GUID]$_.schemaIDGUID,$_.name)}
Get-ADObject -SearchBase "CN=Extended-Rights,$((Get-ADRootDSE).configurationNamingContext)" -LDAPFilter '(objectClass=controlAccessRight)' -Properties name, rightsGUID |
ForEach-Object {$schemaIDGUID.add([System.GUID]$_.rightsGUID,$_.name)}
$ErrorActionPreference = 'Continue'
ForEach ($OU in $OUs) {
$report += Get-Acl -Path "AD:\$OU" |
Select-Object -ExpandProperty Access |
Select-Object @{name='organizationalUnit';expression={$OU}}, `
@{name='objectTypeName';expression={if ($_.objectType.ToString() -eq '00000000-0000-0000-0000-000000000000') {'All'} Else {$schemaIDGUID.Item($_.objectType)}}}, `
@{name='inheritedObjectTypeName';expression={$schemaIDGUID.Item($_.inheritedObjectType)}}, `
*
}
# report with assigned OU permissions
You can get the delegated permissions report with a graphical Out-GridView cmdlet:
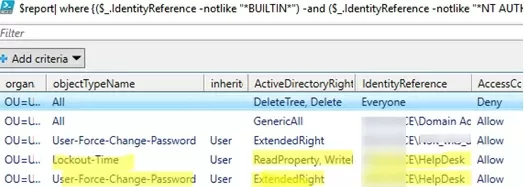
$report| where {($_.IdentityReference -notlike "*BUILTIN*") -and ($_.IdentityReference -notlike "*NT AUTHORITY*") }| Out-GridView
Or export the list of permissions to a CSV file for further analysis in Excel ( you can write data directly to an Excel file from a PowerShell script):
$report | Export-Csv -Path "C:\reports\AD_OU_Permissions.csv" –NoTypeInformation
The resulting report shows that the HelpDesk group has been delegated the permissions to reset user passwords (ObjectTypeName=User-Force-Change-Password) in the OU.
You can use the dsacls tool to delegate rights to an OU. For example:
dsacls "ou=users,ou=paris,dc=woshub,dc=com" /I:S /G "WOSHUB\HELPDESK:CA;Reset Password;user" "WOSHUB\HELPDESK:WP;pwdLastSet;user" "WOSHUB\HELPDESK:WP;lockoutTime;user
You can also assign permissions to the Organizational Unit container using PowerShell (in this example, the permissions to reset the password are delegated):
$ou = "AD:\OU=users,OU=Paris,DC=woshub,DC=com"
$group = Get-ADGroup helpdesk
$sid = new-object System.Security.Principal.SecurityIdentifier $group.SID
$ResetPassword = [GUID]"00299570-246d-11d0-a768-00aa006e0529"
$UserObjectType = "bf967aba-0de6-11d0-a285-00aa003049e2"
$ACL = get-acl $OU
$RuleResetPassword = New-Object System.DirectoryServices.ActiveDirectoryAccessRule ($sid, "ExtendedRight", "Allow", $ResetPassword, "Descendents", $UserObjectType)
$ACL.AddAccessRule($RuleResetPassword)
Set-Acl -Path $OU -AclObject $ACL
Similarly, you can delegate other permissions to AD organizational containers using PowerShell.