By default, the login screen on Windows 10/11 and Windows Server 2019/2016/2012R2 displays the account of the last user who logged in to the computer. You can configure different behavior of this feature: you can show the last logon username, hide it, or even list all local/logged domain users on your device’s welcome screen.
Do Not Display the Last Username on Windows Logon Screen
End users are comfortable when the last logged account name is displayed on the Windows Logon Screen and doesn’t need to be typed in manually. But this makes it easier for an attacker to access the computer. To access your device, he only needs to find the correct password. To do this, there are various ways of social engineering, brute-force attacks, or a banal sticky piece of paper with a password on the monitor.
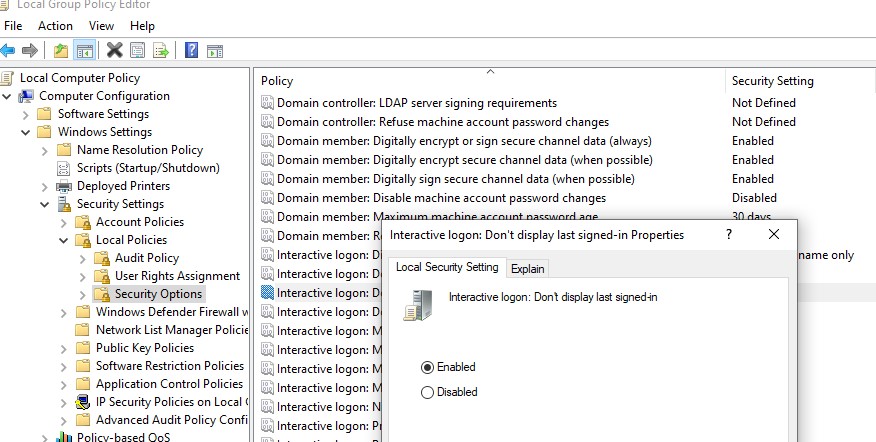
You can hide the last logged username on a Windows logon screen through the GPO. Open the domain (gpmc.msc) or local Group Policy editor (gpedit.msc) and go to the section Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options. Enable the policy “Interactive logon: Do not display last user name”. This policy is disabled by default.
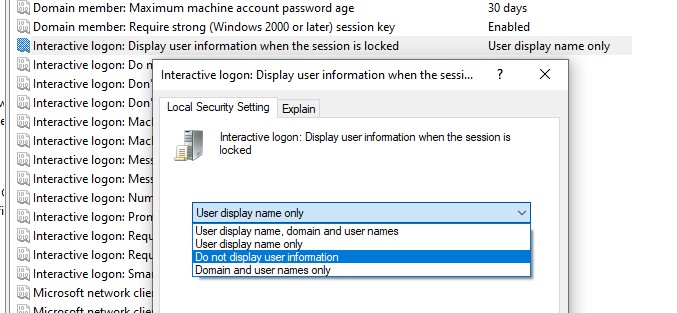
The username is also displayed on the computer if its screen is locked (by pressing Win+L or via the lock screen GPO). You can hide the username on a computer lock screen. To do this, in the same section of the GPO, you must enable the policy “Interactive logon: Display user information when the session is locked” and set the value “Do not display user information.
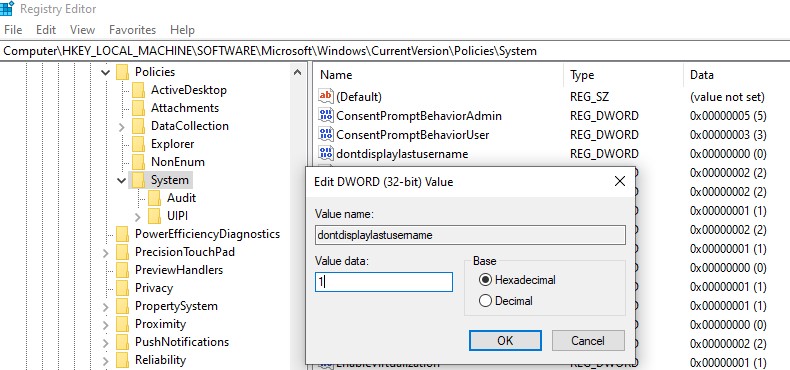
A registry parameter named DontDisplayLockedUserId in the same registry key with a value of 3 matches this policy parameter.
- 1 — show user display name, domain, and usernames
- 2 — show only user display names
- 3 — do not display users.
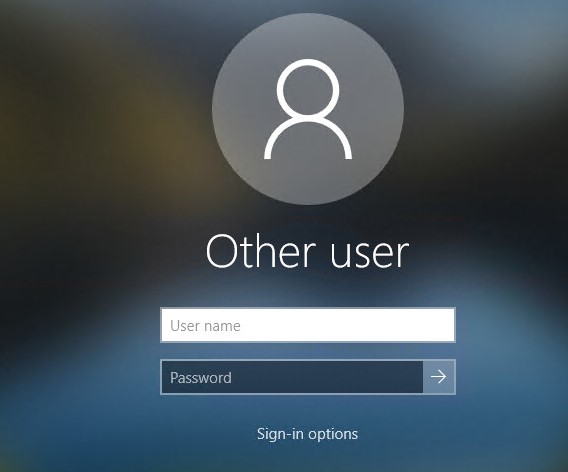
The computer login screen and Windows lock screen now display the blank username and password fields.
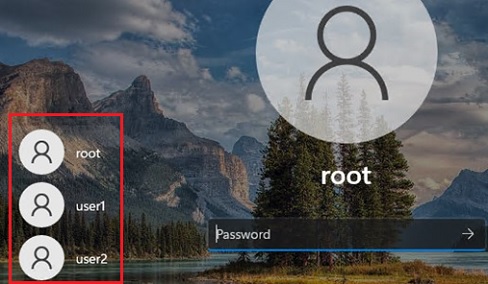
Show All Users on Windows 10/11 Sign-in Screen
By default, modern versions of Windows (tested on Windows 11 21H2 and Windows 10 21H1) always show the list of enabled local users in the bottom left corner of the login screen. Only hidden (see below) or disabled users are not displayed.
To log in to the computer, the user just needs to click on the required user account and specify its password. This only works on computers that are not joined to the Active Directory domain.
If the list of local users is not displayed on the computer logon screen, check the settings of the following local Group Policy options (use the gpedit.msc):
- Interactive Logon: Do not display last signed-in =
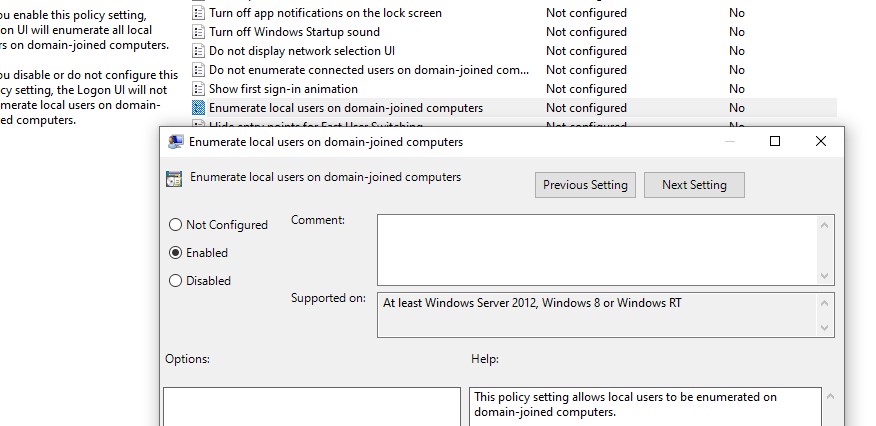
Disabled(Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options); - Enumerate local users on domain-joined computers =
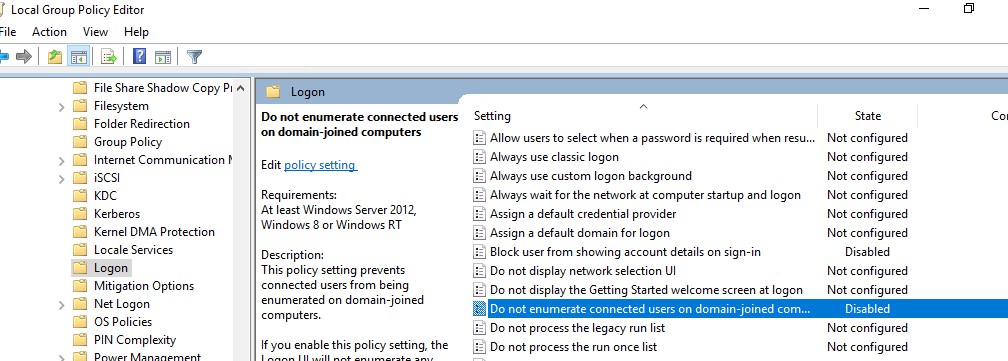
Enabled(Computer Configuration -> Administrative Templates -> System -> Logon) - Do not enumerate connected users on domain-joined computer =
Disabled/Not Configured(in the same GPO section)
Restart your computer to apply the new Group Policy settings.
In some old Windows 10 builds (from 1609 up to 1903), there was another problem with displaying all local users on the Windows Welcome screen, related to user switching mode.
To display all local user accounts on the Windows login screen, you need to change the value of Enabled parameter to 1 in the following registry key: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\LogonUI\UserSwitch. This option allows you to switch the current user on the Windows sign-in screen. However, Windows automatically resets the value of the Enabled parameter to 0 at each user logon.
In order to fix this problem, you need to create a scheduler task that will change the parameter value to 0 on each user logon.
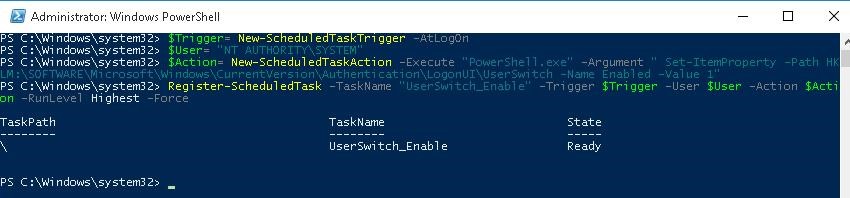
You can create a new Scheduler task with PowerShell:
$Trigger= New-ScheduledTaskTrigger -AtLogOn
$User= "NT AUTHORITY\SYSTEM"
$Action= New-ScheduledTaskAction -Execute "PowerShell.exe" -Argument "Set-ItemProperty -Path HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\LogonUI\UserSwitch -Name Enabled -Value 1"
Register-ScheduledTask -TaskName "UserSwitch_Enable" -Trigger $Trigger -User $User -Action $Action -RunLevel Highest –Force
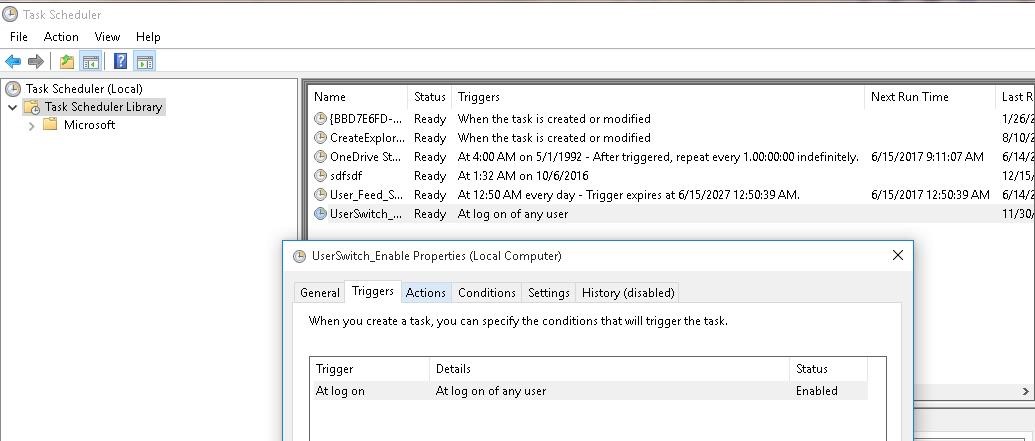
Make sure that the task appeared in Windows Task Scheduler (taskschd.msc).
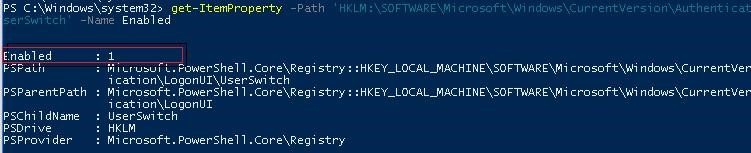
Log off and then log on again. The task must start automatically and change the value of Enabled registry parameter to 1. Check the current value of the parameter using Get-ItemProperty. As you can see, it is 1:
get-ItemProperty -Path 'HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\LogonUI\UserSwitch' -Name Enabled
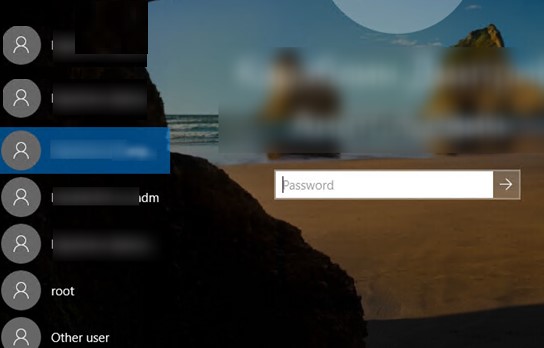
Show Logged In Domain Users on Windows Login Screen
If multiple domain users share the same computer, you can display a list of users with active sessions on the welcome screen. An active session means that users are logged into the computer. It can be a shared computer (used in user switching mode), kiosks, Windows Server RDS hosts, or Windows 11 and 10 devices with multiple RDP connections allowed).
To do this, check that in the Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options the following policies are disabled:
- Interactive logon: Don’t display last signed-in: Disabled
- Interactive logon: Don’t display username at sign-in: Disabled
Then disable the policies in the section Computer Configuration -> Administrative Templates -> System -> Logon:
- Block user from showing account details on sign-in: Disabled
- Do not enumerate connected users on domain-joined computer: Disabled
After that, the welcome screen will display a list of logged-on users. Both active sessions and sessions of users with the disconnected status (for example, by RDP timeout) will be displayed here. The user only needs to log in once, and then just select an account from the list and enter a password.
rsop.msc or gpresult to get the resulting Group Policy settings on your device.Hide Specific User Accounts from the Sign-in Screen on Windows 10 and 11
The Windows Welcome screen always displays users who are members of one of the following local groups: Administrators, Users, Power Users, Guests.
You can hide specific users from the list on the welcome screen through the registry. To do this, you need to use the HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\UserList registry key. You need to create a DWORD parameter with username and value 0 for each user you want to hide.
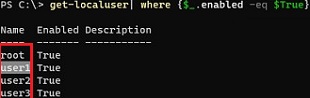
You can list local user names with PowerShell or cmd:
Net user
Or:
Get-LocalUser | where {$_.enabled –eq $true}
To hide a specific user account from the Windows 11 or 10 welcome screen (for example, user1), run the command:
reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\UserList" /t REG_DWORD /f /d 0 /v UserName
If the built-in Windows administrator account is enabled on the computer, and this is not the only account with local administrator permissions on the computer (!!!), you can hide it too:
reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\UserList" /t REG_DWORD /f /d 0 /v administrator
If you want to hide all users except the last one logged into the computer, configure the following GPO settings in Computer Configuration -> Administrative Templates -> System -> Logon:
- Enumerate local users on domain—joined computers = Disabled
- Do not enumerate connected users on domain-joined computer = Enabled
21 comments
Mine displays all of the accounts by default. How come?
This is absurd. If this is actually the setting- which has taken an hour of googling to find- to show all the local users on the login screen, the fact that it has to be set and then a timed script created to keep it set is… nucking futs. What a hate joke of an OS.
I agree completely. It’s as if none of the developers considered the basics only the settings one would need to perform a hostile takeover of IBM. I’ve been chasing a way for days to login as any other user in Windows 10. There’s no way to switch users and no solution anywhere. Ask Microsoft? Their response is “There’s no way to switch users in Windows 10? Have you tried logging out?” (Almost took a hostage.)
Arf! This is not about local account, but this tuto is about domain account. When you have severals doamain users on the same domain computer, its interresting to show all users account on the start menu.
By default, they have to choose “other user” and type both their ID and password. So with this method, they just have to click on appropriate username and type password.
For information, this doesn’t work. Scheduled task is working on all users, the reg value switch from 0 to 1 at startup for all users but on startup screen, only last user logged appear.
Not working. MS probably killed it in an update.
You have to change the permissions of the userswitch reg key : change the owner to Admin group and enable full control of the key for Admin and disable the write permission for SYSTEM. This is working since Windows 8.
@Roland – not an adminstrator but often end up having to do deskside support. How do I do what you suggested?
Try to run this powershell script as admin :
## Taken from P/Invoke.NET with minor adjustments.
$Definition = @’
using System;
using System.Runtime.InteropServices;
public class AdjPriv {
[DllImport(“advapi32.dll”, ExactSpelling = true, SetLastError = true)]
internal static extern bool AdjustTokenPrivileges(IntPtr htok, bool disall,
ref TokPriv1Luid newst, int len, IntPtr prev, IntPtr rele);
[DllImport(“advapi32.dll”, ExactSpelling = true, SetLastError = true)]
internal static extern bool OpenProcessToken(IntPtr h, int acc, ref IntPtr phtok);
[DllImport(“advapi32.dll”, SetLastError = true)]
internal static extern bool LookupPrivilegeValue(string host, string name,
ref long pluid);
[StructLayout(LayoutKind.Sequential, Pack = 1)]
internal struct TokPriv1Luid {
public int Count;
public long Luid;
public int Attr;
}
internal const int SE_PRIVILEGE_ENABLED = 0x00000002;
internal const int TOKEN_QUERY = 0x00000008;
internal const int TOKEN_ADJUST_PRIVILEGES = 0x00000020;
public static bool EnablePrivilege(long processHandle, string privilege) {
bool retVal;
TokPriv1Luid tp;
IntPtr hproc = new IntPtr(processHandle);
IntPtr htok = IntPtr.Zero;
retVal = OpenProcessToken(hproc, TOKEN_ADJUST_PRIVILEGES | TOKEN_QUERY,
ref htok);
tp.Count = 1;
tp.Luid = 0;
tp.Attr = SE_PRIVILEGE_ENABLED;
retVal = LookupPrivilegeValue(null, privilege, ref tp.Luid);
retVal = AdjustTokenPrivileges(htok, false, ref tp, 0, IntPtr.Zero,
IntPtr.Zero);
return retVal;
}
}
‘@
# Take ownership privilege
$ProcessHandle = (Get-Process -id $pid).Handle
$type = Add-Type $definition -PassThru
for ($i=1; $i -le 10;$i++){
$status=$type[0]::EnablePrivilege($processHandle, “SeTakeOwnershipPrivilege”)
if ($status){break}
if ($i -eq 10){read-host “Unable to take ownership privilege”;exit}
start-sleep 1|out-null
}
#
$keypath=”SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\LogonUI\UserSwitch”
#
# Get localized admin group name
$admin=(get-wmiobject win32_group| Where-Object {$_.sid -eq “s-1-5-32-544”}).name
# Change Owner to the local Administrators group
$regKey = [Microsoft.Win32.Registry]::LocalMachine.OpenSubKey(“$keypath”, “ReadWriteSubTree”, “TakeOwnership”)
$regACL = $regKey.GetAccessControl()
$regACL.SetOwner([System.Security.Principal.NTAccount]”$admin”)
$regKey.SetAccessControl($regACL)
# Change Permissions for the local Administrators group
$regKey = [Microsoft.Win32.Registry]::LocalMachine.OpenSubKey(“$keypath”, “ReadWriteSubTree”, “ChangePermissions”)
$regACL = $regKey.GetAccessControl()
$regRule = New-Object System.Security.AccessControl.RegistryAccessRule (“$admin”,”FullControl”,”ContainerInherit”,”None”,”Allow”)
$regACL.SetAccessRule($regRule)
# Change Permissions for System
$regRule = New-Object System.Security.AccessControl.RegistryAccessRule (“SYSTEM”,”SetValue”,”ContainerInherit”,”None”,”Deny”)
$regACL.SetAccessRule($regRule)
$regKey.SetAccessControl($regACL)
New-ItemProperty -Path “HKLM:\$keyPath” -Name “Enabled” -Value 1 -PropertyType DWORD -Force |out-null
You need to run this as admin since admin privilege is required to get ownership of the userswitch key owned by the system account.
Thank you, Roland! I may have it fixed, after making some changes to the group policy. If not, this topic is bookmarked. 🙂
is this working on domain users i did everything and still the users not showing at startup.
Hi Laura M, Can you explain what group policy changes you made to fix this?
Hi Nate. i actually followed the instructions I found on this site (first reply to the topic):
https://social.technet.microsoft.com/Forums/en-US/2ab569f5-ec46-4f54-a544-42504589d920/windows-10-logon-screen-retain-previously-logged-domain-users?forum=win10itprosetup
Please be aware that I am *not* a sysadmin. I am just a regular user who ends up having to try and play deskside support, so there may well be things I am making more diffiucult than they need to be. 🙁
Things I did notice-
1. The users I added didn’t actually show on the list on the list until after they logged in the first time.
2. When they did log in the first time, i found that it didn’t work if anyone else was currently logged in (it has to go through the set up for each user, and have them set a PIN). So, since their name wasn’t on the list, I had them select Other user. Then I had them click “Sign in options” and click the globe icon. Assuming that the ids were created using their email addresses, I had them enter that and followed prompts from there.
That’s what worked for me, but your experience may be different.
This (userswitch) was working for me until 1903 update. Now the reg values are correct, but some users (without passwords) are automatically logged in on start up.
Why should the user have to know ANYTHING that is going on behind the GUI? This is as bad as old MSDOS days!
I logged into my work computer cortana usuing my personal Microsoft account, which apparently created a new user profile (also started displaying my beach vacation photos as the background) so I deleted the user profile and restarted the computer now the only option to logon is usuing the same user profile I just deleted (my personal) but now asking for a password that I did not create nor is my existing Microsoft personal password. my original default login profile is not displayed as an option either.. Effectively I’m locked out of my brand new office computer.
None of the the above worked for me.
I have searched high and low on the web for a solution to get multiple users
to show on login screen in Windows 10. The best I could do is a workaround
based on info on a Tenforum thread. I provide this in case it helps
someone else. It is not elegant, but suffices until a real solution comes along.
My thanks to Shawn Brink.
0. Create new user [Admin] with password
1. type ‘run’ or {Win+R} to get the Run dialogue box
2. type ‘netplwiz’ and click on OK
3. Check [if not already checked] “Users must enter a user name and password to use this computer” checkbox
4. select user you are not signed on as [see #0 above]
5. Uncheck “Users must enter a user name and password to use this computer checkbox”
6. Click OK
7. Click OK [leave password boxes blank]
8. Reboot.
Login will fail, but available signons will show. Repeat 1-8 on New User.
I have not tried this for nonAdmin accounts nor for more than two User Accounts.
It helped me, i was looking for this login solution everywhere and only this one worked finally. I am so happy that i am connecred ro right peopke and solutions and so is my laptop.
https://answers.microsoft.com/en-us/windows/forum/all/all-local-user-accounts-missing-from-login-screen/9964e4c1-9aed-4fa0-b4c4-84180edf92f0
Thank you for this wonderful solution. It work for me perfectly. Godbless
Thank you