Using local accounts (including the local administrator) to access another computer over network in Active Directory environments is not recommended on a number of reasons. The same local administrator username and password are often used on many computers, which can put multiple devices at risk if a single computer is compromised (Pass-the-hash attack threat). Moreover, access to the network resources with local accounts is hard to personify and centrally monitor, because such events are not logged on AD domain controllers.
To mitigate the risk, administrators can rename the default local Windows Administrator account. To regularly change the local administrator password on all computers in the domain, you can use the MS LAPS tool (Local Administrator Password Solution). But these solutions won’t be able to solve the problem of restricting network access for all local user accounts, since there can be more than one local account on a computer.
You can restrict network access for local accounts using the Deny access to this computer from the network policy. But this policy requires to explicitly list all accounts that need to be denied network access to the computer.
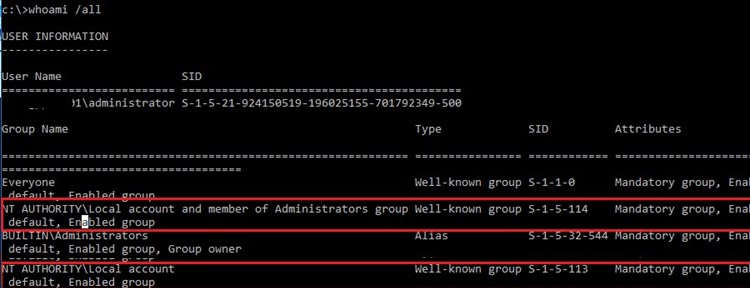
In Windows 8.1 and Windows Server 2012 R2, two new well-known security groups with new SIDs appeared. One includes all local users, and the second includes all local administrators.
| S-1-5-113 | NT AUTHORITY\Local account | All local accounts |
| S-1-5-114 | NT AUTHORITY\Local account and member of Administrators group | All local accounts with the administrator privileges |
Now, to restrict access for local accounts, you can use their common SIDs.
These groups are added to the user’s access token during logon to the computer under a local account.
To make sure that in Windows 10/Windows Server 2016 your local administrator account is assigned two new security groups (NT AUTHORITY\Local account (SID S-1-5-113) and NT AUTHORITY\Local account and member of Administrators group (SID S-1-5-114)), run the command:
Whoami /all
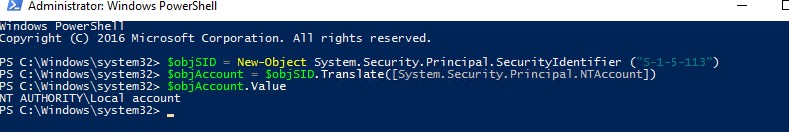
You can check if these security groups exist on your Windows device by SID using the following PowerShell script:
$objSID = New-Object System.Security.Principal.SecurityIdentifier ("S-1-5-113")
$objAccount = $objSID.Translate([System.Security.Principal.NTAccount])
$objAccount.Value
If the script returns NT Authority\Local account, then this local group (with S-1-5-113 SID) exists on your computer.
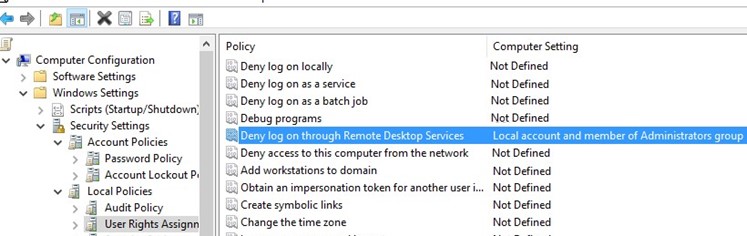
In order to block the remote network access under local user accounts containing these SIDs in the token, you can use the settings from the GPO section Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> User Rights Assignment.
Deny Remote Desktop (RDP) Access for Local Users and Administrators
The Deny log on through Remote Desktop Services policy allows you to specify users and groups that are explicitly denied to logon to a computer remotely via Remote Desktop. You can deny RDP access to the computer for local and domain accounts.
If you want to restrict RDP connections for local users only (including local administrators), open the local GPO editor gpedit.msc (if you want to apply these settings on computers in the Active Directory domain, use the domain Group Policy Editor – gpmc.msc). Go to the GPO section User Rights Assignment and edit the Deny log on through Remote Desktop Services policy.
Add the built-in local security groups “Local account and member of Administrators group” and “Local account” to the policy. Update local Group Policy settings using the command: gpupdate /force.
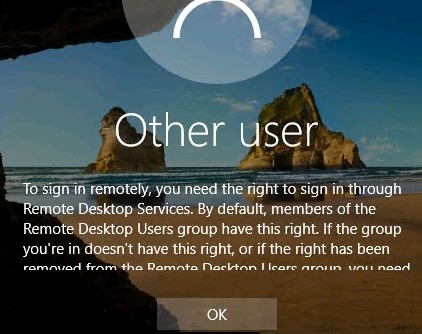
Now, if you try to connect to your computer under local user via RDP, an error will appear:
To sign in remotely, you need the right to sign in through Remote Desktop Services. By default, members of the Remote Desktop Users group have this right. If the group you’re in doesn’t have this right, or if the right has been removed from the Remote Desktop Users group, you need to be granted this right manually.
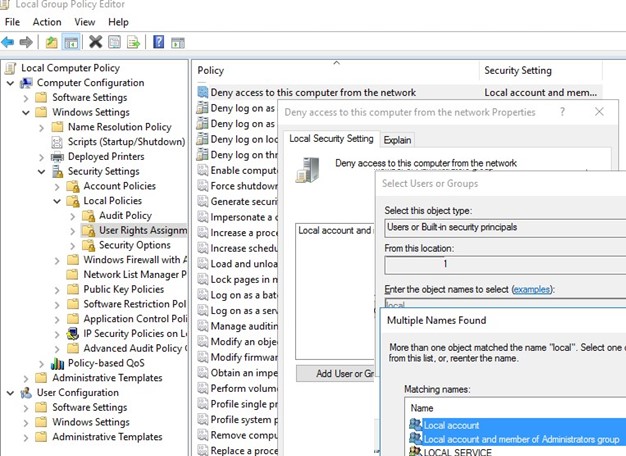
Deny Access to Computer from the Network
You can deny network access to a computer under local credentials with the Deny access to this computer from the network policy.
Add the local groups “Local account” and “Local account and member of Administrators group” to the Deny access to this computer from the network policy. Also, you should always deny anonymous access and access under a guest account.
After applying the policy, you won’t be able to remotely connect to this computer over the network under any local Windows account. When trying to connect to a shared network folder or map a network drive from this computer under a local account, an error will appear:
Microsoft Windows Network: Logon failure: the user has not been granted the requested logon type at this computers.
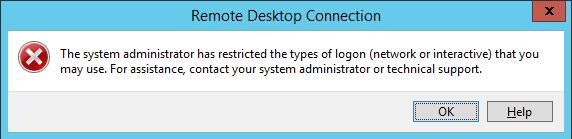
When trying to establish a Remote Desktop connection under the local administrator account (.\administrator), an error message appears.
The system administrator has restricted the types of logon (network or interactive) that you may use. For assistance, contact your system administrator or technical support.
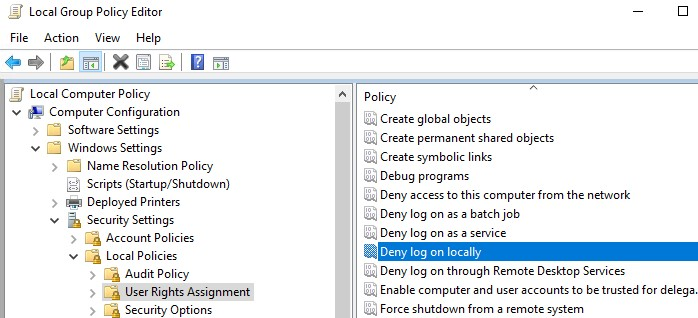
Deny Users to Sign in Locally to Windows 10
Using the Deny log on locally policy, you can also restrict interactive logins to the computer/server under local Windows accounts. Go to the GPO User Rights Assignment section, edit the Deny log on locally policy. Add the required local security group to it.
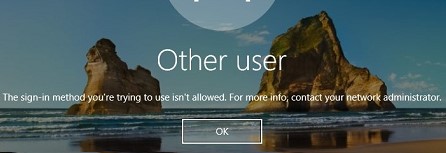
Now, if a user or administrator tries to logon to the computer under a local account, a message will appear.
The sign-in method you are trying to use isn’t allowed. For more info, contact your network administrator.
Thus, you can deny network access under local Windows accounts to computers and domain-member servers, and increase the security of the corporate environment.
8 comments
Thanks for the good article
Great article.
And how to allow .\administrator on a specific computer only?
You can exclude a user or group from Group Policy Object. To do this, find you GPO you want to apply an exception on in the Group Policy Management Console. Go to the Delegation tab -> Advanced -> Add -> Select a computer name to exclude -> Select “Deny” in the “Apply group policy” permission.
What if I want to allow only local administrator (i.e. RID-500 account) to logon over network and to deny logon over network to all other local (and local only) accounts ? There is no SID for “every local account but RID-500 admin” so I presume it is not an easy job to do.
Thanks
Wonderful article. In order to block the remote network access under local user accounts containing these SIDs in the token, you can use the settings from the GPO section Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> User Rights Assignment.
I am just a regular user who would like to stop the user that is logging onto my computer through windows 10 NT Authority Logon Special Logon then changing the group policy to establish an organization workgroup as administrator that takes my right to use my computer or change settings without administrator permission. I found that I am possibly being forced to use a virtual machine that has a virtual internet with a recreated web page of my online Brokerage account. recreating a persons bank account is not the same as a Brokerage account that is time intensive throughout the trading hours and imediatly noticeable that i am not logged into the real online account instantly changing values of my portfolio assets and available trading funds change as soon as a order is filled . For someone to create a virtual environment to access or control my use of my Portfolio would take twenty four hour a day monitoring especially during trading hours . I DO NOT KNOW HOW TO STOP THE USE OF THE NT AUTHORITY LOGON SPECIAL LOGON PRIVILEGE ASSUME SYSTEM OWNER THAT ALLOWS THE REMOTE USER TO CONTROL MY COMPUTER AS A AN ORGANIZATION DEVICE THAT TAKES MY RIGHT TO USE IT AWAY FROM ME. How do I IDENTIFY and STOP the remote USER that is HIGHJACKING and STEALING MY COMPUTER SYSTEM by accessing my computer through WINDOWS 10 NT AUTHORITY using LOGON SPECIAL LOGON PRIVILEGES TO ASSUME SYSTEM OWNER to change the Policies that allow that user to deny me the right to use a computer I paid for and own
Remotely managed and used as an organization device hosting service with an unknown numer of cients who can Hyper-V to create an endless number of Virtual Machines interconnected and used by the remote manager to create a Hive