In this article, we will look at how to get a list of users and groups that have local administrator rights on Windows workstations and servers on your network.
Find Local Administrators on the Local Computer
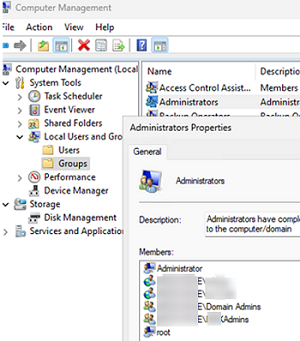
In Windows, you can use the Computer Management snap-in (compmgmt.msc) to view, add, or remove users in the local Administrators group. Expand Computer Management -> Local users and Group -> Groups. Then select the Administrators group.
By default, when a Windows computer is joined to an Active Directory domain, administrator rights are granted to local administrator users and the Domain Admins security group.
All other users or groups are added to the Administrators group separately (manually, via Group Policy, scripts, etc.).
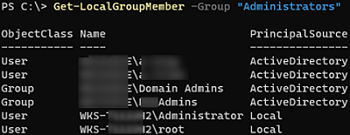
You can use the Get-LocalGroupMember cmdlet from the built-in Microsoft.PowerShell.LocalAccounts module to list the members of the local Administrators group:
Get-LocalGroupMember -Group "Administrators"
Please note that the Principal parameter contains the source of this user/group, which can be the Local, Active Directory, or Azure AD domain.
This is how you can list only the local users who have administrator privileges:
Get-LocalGroupMember Administrators | Where-Object { (Get-LocalUser $_.SID -ErrorAction SilentlyContinue).Enabled }
You can filter the list to include only AD users:
Get-LocalGroupMember Administrators | Where-Object {$_.PrincipalSource -eq "ActiveDirectory"} | select PrincipalSource,class,name,SID
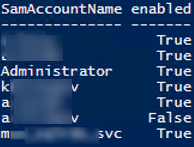
If the Active Directory for Windows PowerShell module from the RSAT package is installed on your computer, you can get additional information about AD users or groups by their SIDs.
In this example, the script finds the members of all Active Directory groups that are local administrators on this computer (the Get-ADGroupMember cmdlet is used to get the list of AD group users). Then the Get-ADUser is used to get the SamAccountName and the status of the account (Enabled = True/False).
$admins=Get-LocalGroupMember Administrators | Where-Object {$_.PrincipalSource -eq "ActiveDirectory"}
Foreach ($admin in $admins)
{
If ($admin.objectclass –eq "User") {get-aduser $admin.sid|select SamAccountName,enabled }
If ($admin.objectclass –eq "Group") {Get-ADGroupMember $admin.sid | foreach { Get-ADUser $_ |Select-Object SamAccountName,enabled }}
}
Get Local Administrators Group Member from Remote Computer
The above example gets the list of users with administrator rights on the local computer. Now let’s look at how to get the members of the local Administrators group from a remote Windows computer.
To run commands on remote computers, you must configure PowerShell Remoting and open the TCP 5985 firewall port. You can enable and configure WinRM (PSRemoting) using GPO, and then change your Windows Defender Firewall Group Policy settings to open an additional port.
Use the Invoke-Command PowerShell cmdlet to run a command on a remote computer. To list the administrators on the remote computer named wsk-m2211, use the following command:
Invoke-Command -ComputerName wsk-m2211 -ScriptBlock {Get-LocalGroupMember -Name 'Administrators'|select Name,ObjectClass,PrincipalSource|ft}
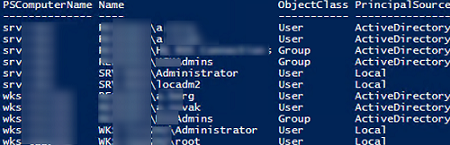
Now let’s see how to get a list of administrators from multiple computers. For convenience, we will exclude the Domain Admins group from the results:
$results = Invoke-Command wsk-m2211,srv-sql01,srv-rds02 -ScriptBlock {Get-LocalGroupMember -Name 'Administrators'|where {$_.name –notlike "*Domain Admins*"}|select Name,ObjectClass,PrincipalSource}
$results | Select-Object PSComputerName,Name,ObjectClass,PrincipalSource
Use the Export-CSV command to export the resulting list of users and groups to a CSV file:
$results | Export-CSV "C:\PS\admins.CSV" -NoTypeInformation -Encoding UTF8
You can query multiple computers or servers from a domain simultaneously. In this example, I want to get a list of admins on all Windows Server hosts in AD. Use the Get-ADComputer cmdlet to list enabled Windows Server computers in Active Directory:
$computers = (Get-ADComputer -Filter 'operatingsystem -like "*Windows server*" -and enabled -eq "true"').Name
Next, get the list of local Administrators group members on each host:
$results = Invoke-Command -ComputerName $computers -ScriptBlock {Get-LocalGroupMember -Name 'Administrators'|where {$_.name –notlike "*Domain Admins*"}|select Name,ObjectClass,PrincipalSource} -ErrorAction SilentlyContinue
Removing Users from the Local Administrators Group
It is extremely important for enterprise administrators to keep track of the members of the local Administrators group on domain computers. The main idea is to minimize the number of users with local admin rights.
You can manually remove a user from the local admins group with the command:
Remove-LocalGroupMember -Group Administrators -Member username
You can remove a user from a group on a remote computer:
Invoke-Command -ComputerName wsk-m2211 –ScriptBlock {Remove-LocalGroupMember -Group Administrators -Member username}
However, there’s a more advanced method you can use. Suppose you have created a list of users with administrative privileges on computers and saved it in the $results variable.
$results = Invoke-Command wsk-m2211,wsk-m2233 -ScriptBlock {Get-LocalGroupMember -Name 'Administrators'|where {$_.name –notlike “*Domain Admins*”}|select Name,ObjectClass,PrincipalSource,SID}
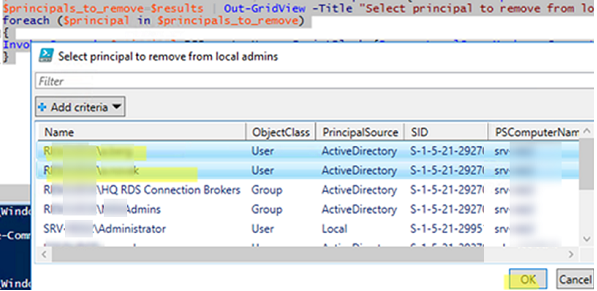
Then display a list of users and computers in the form of an Out-GridView list:
$principals_to_remove=$results | Out-GridView -Title "Select principal to remove from local admins" -OutputMode Multiple
The next thing you have to do is to select the users you want to remove from the Administrators group (press and hold CTRL to select multiple rows in the table) and run the code:
foreach ($principal in $principals_to_remove)
{
Invoke-Command $principal.PSComputerName -ScriptBlock {Remove-LocalGroupMember -Group Administrators -Member $using:principal.name}
}
$using:principal.name construct allows you to pass a local variable value from your computer to a remote PSRemoting session.This will remove the users you have selected from the local Administrators group on the remote computers.
1 comment
Gathering the members of the “local administrators” group by its name, is just … a very bad idea !
The name of this group is depending of the local culture, but the SID of this group is always the same : it’s a Well-known SID.
One of the first rule to know when you wand to script something is “think code re-use”.